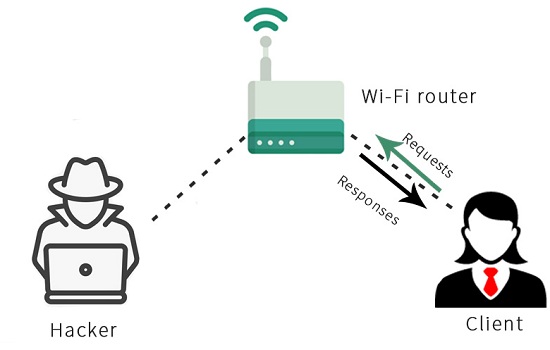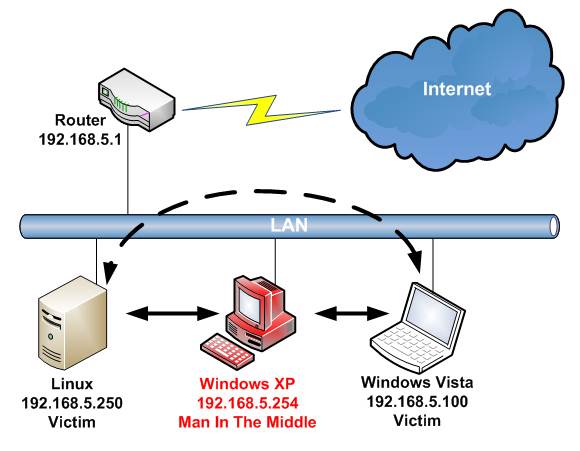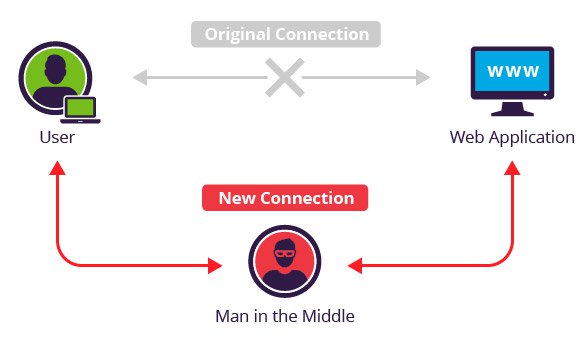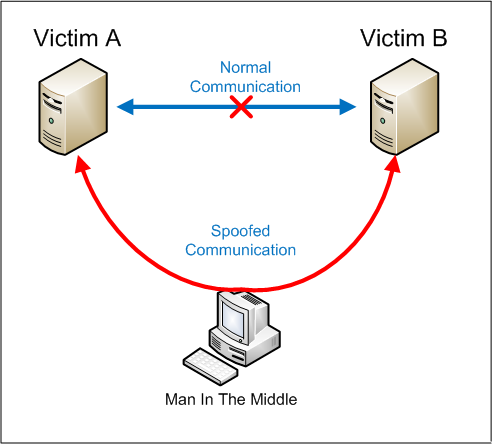
Cyber Security : Man In The Middle Attack Explained | Pune Mumbai Hyderabad Delhi Bangalore India | Valency Networks
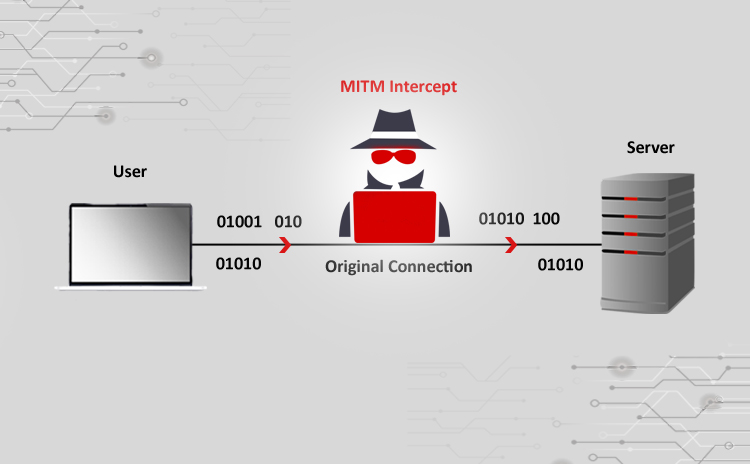
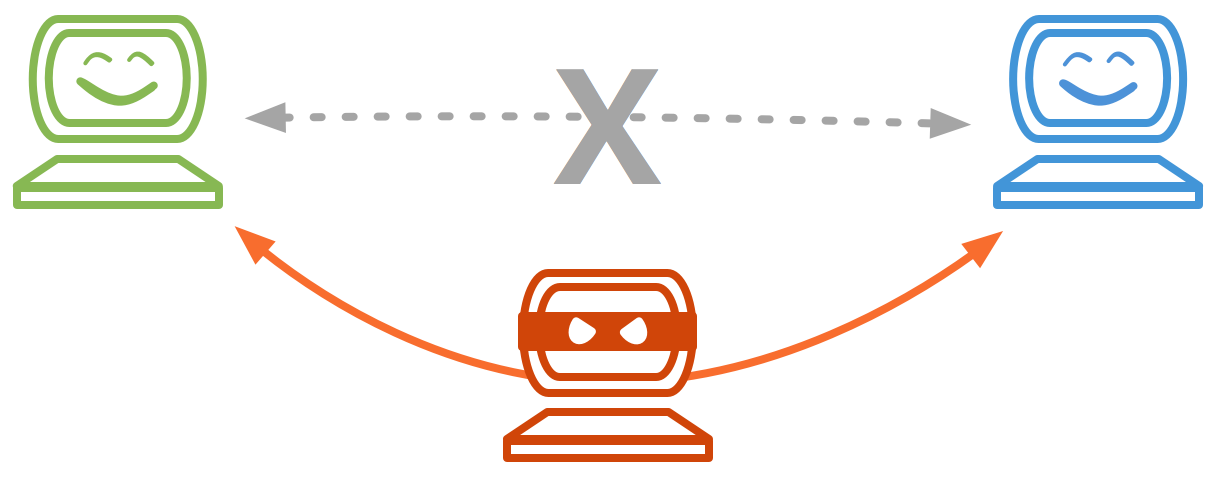
Cyber Attacks Explained - Man In The Middle Attack | Cyber Security Blogs - | Valency Networks | Best VAPT Penetration Testing Cyber Security Company | Pune Mumbai Hyderabad Delhi Bangalore Ahmedabad

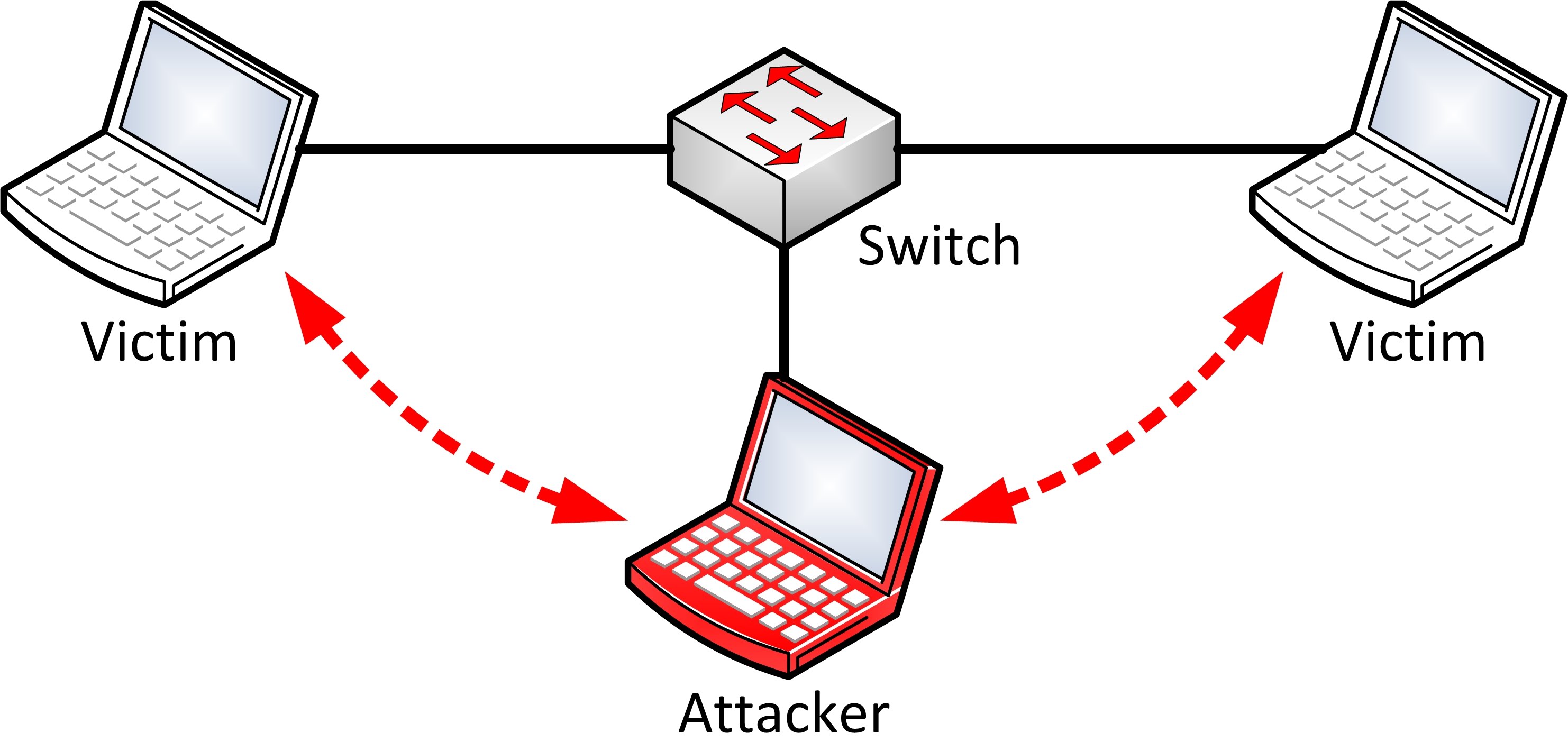
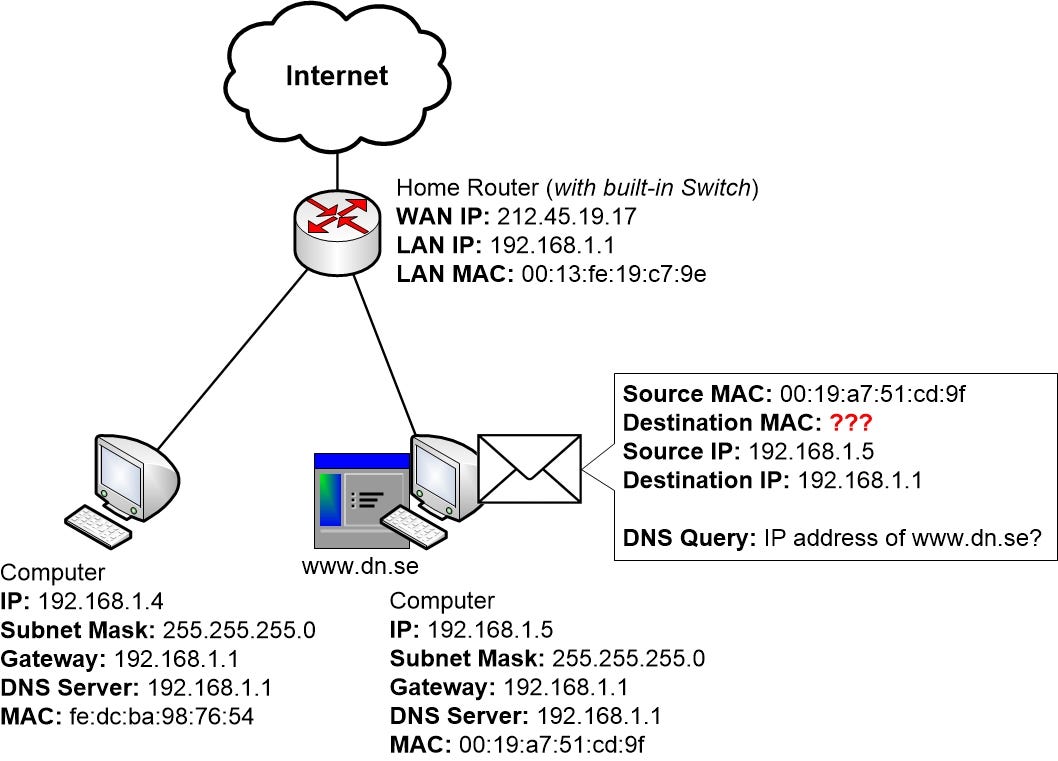
ARP Spoofing and Performing Man-in-the-middle Attacks. | by Arnav Tripathy | Noteworthy - The Journal Blog
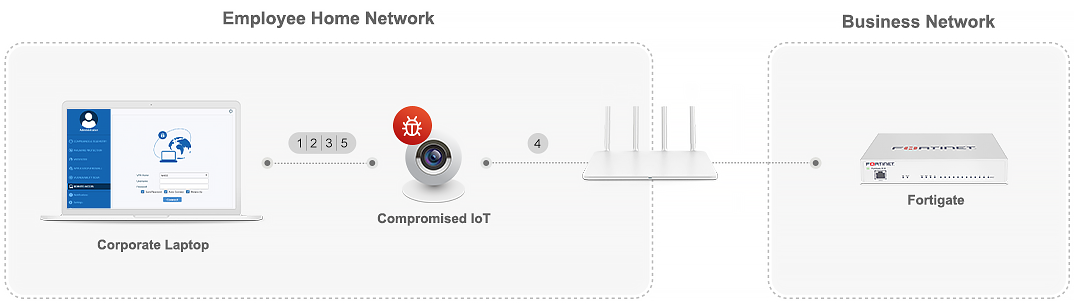
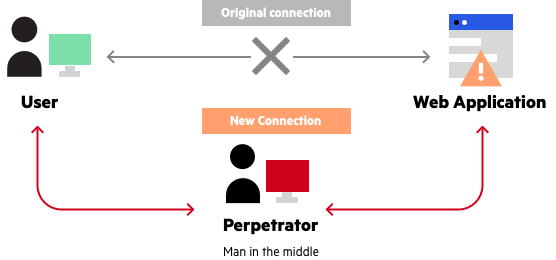
Fortinet VPN with default certificate exposes 200,000 businesses to hack - Security AffairsSecurity Affairs

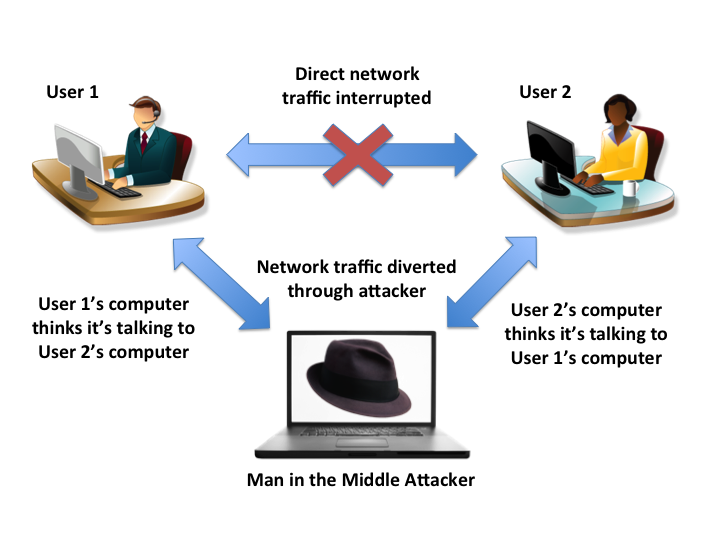


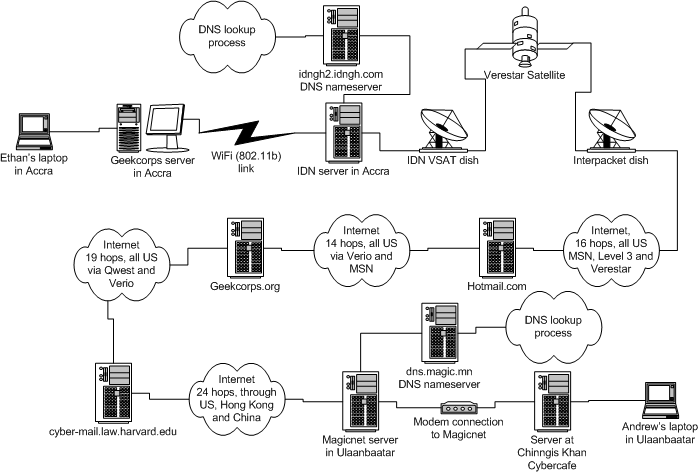

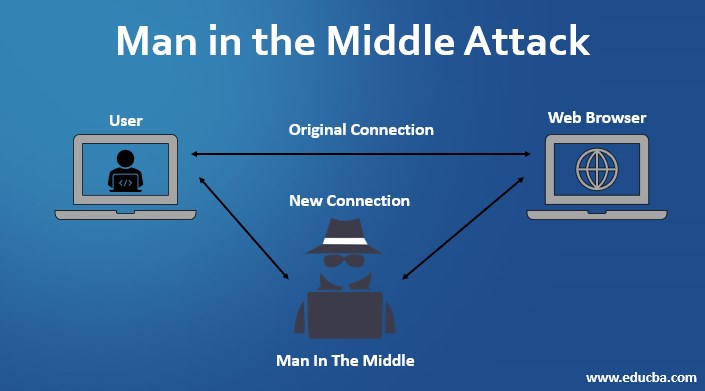
%20Attack.jpg)